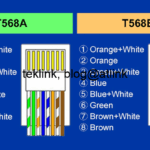
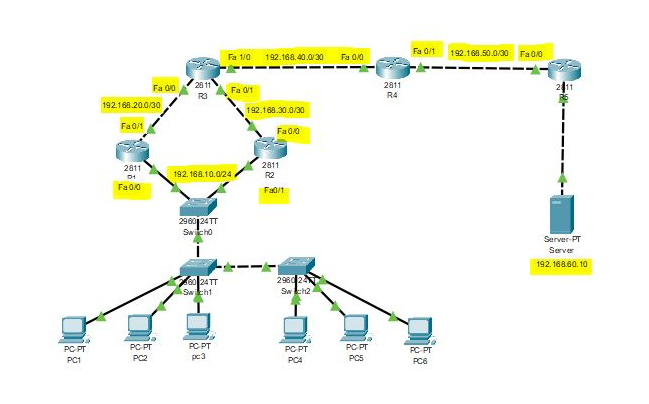
In this blog, we’ll discuss in detail the operation of HSRP one of the most known FHRP (First Hop Routing Protocols) protocols proposed by Cisco to help secure (in terms of redundancy) the gateway (for hosts or servers) within a LAN. The objective is simple: configure one gateway address and provision as many real routers…