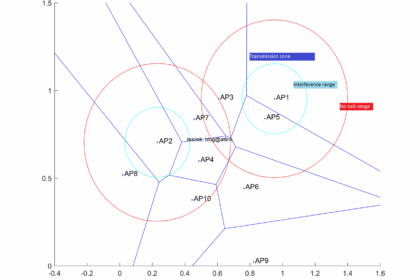
In this post, we present the work on radio coverage in Wlans, accessible at this address: A novel beamforming based model of coverage and transmission costing in IEEE 802.11 WLAN networks, about how t...
Wireless technology is everywhere, overwhelming, in the heart of every IT architecture, and this is for many reasons: increase of user mobility, ease of network operation, scalability in deployment, e...
Guide pratique de la réussite d’un Dossier d’Archiecture Technique ou DAT. Au centre de cette activité, le DAT Le DAT s’inscrit en amont dans le processus de définition et réalisatio...
There is no excerpt because this is a protected post....
There is no excerpt because this is a protected post....
Qui de l’IA ou de la Créativité dicte sa volonté? sujet très passionnant et qui ne manquerait de vous intéresser. Mettez vos gants et en garde ! Au 1er round Indéniablement, la créativité est la...
Ansible (1) Aruba (1) Blockchain (2) Checkpoint (3) Cisco (32) Connectivity (38) Creativity (13) Cybersecurity (1) Extreme Networks (1) Fortinet (1) GNS3 (11) Linux (1) MachineLearning (1) Microsoft (4) Productivity (5) Python (1) RFC (1) Scapy (1) VirtualBox (1) Wireshark (7)
- Protected: An Example Network From Scratch… Internet AccessThis content is password protected.
- Protected: An Example Network from Scratch… Build the Wifi NetworkThis content is password protected.
- Protected: An Example Network From Scratch… On-Premise Network Automation With AnsibleThis content is password protected.
- Protected: An Example Network From Scratch… Build your Network SecurityThis content is password protected.
- Travailler Son CVLe CV est une étape importante de toute recherche d’emploi, au moins pour initier le processus (répondre à une offre, candidature spontanée, etc.)… plus encore, c’est une occasion de se poser, de réfléchir son développement, son expérience et de se projeter dans une nouvelle opportunité! Une approche classique du CV Pour nombre de “demandeurs d’emploi”,
| M | T | W | T | F | S | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | |||
| 5 | 6 | 7 | 8 | 9 | 10 | 11 |
| 12 | 13 | 14 | 15 | 16 | 17 | 18 |
| 19 | 20 | 21 | 22 | 23 | 24 | 25 |
| 26 | 27 | 28 | 29 | 30 | 31 | |